ohai.social is one of the many independent Mastodon servers you can use to participate in the fediverse.

A cozy, fast and secure Mastodon server where everyone is welcome. Run by the folks at ohai.is.
Administered by:
Server stats:
1.7Kactive users
ohai.social: About · Status · Profiles directory · Privacy policy
Mastodon: About · Get the app · Keyboard shortcuts · View source code · v4.5.0-nightly.2025-07-11
#ddos
8 posts · 8 participants · 0 posts today
keef<p>So my first evil genius robot honeypot, the word frequency one, seems to be getting hit by a distributed botnet.</p><p>It started around 2-3 requests per second but seems to be ramping up. </p><p>It's using IP addresses from all over the world - could be hacked personal devices? - and a wide range of plausible-looking User Agent strings.</p><p>My server is fine for now - 95% idle CPU.</p><p>Are there people for whom any of the IP or agent data might be useful? Botnet detectorists?</p><p><a href="https://mastodon.online/tags/botnet" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>botnet</span></a> <a href="https://mastodon.online/tags/ddos" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>ddos</span></a> <a href="https://mastodon.online/tags/cybersec" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>cybersec</span></a> <a href="https://mastodon.online/tags/infosec" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>infosec</span></a></p>
Anna Wasilewska-Śpioch<p>Pogłoski o unieszkodliwieniu NoName057(16) okazały się przedwczesne, zresztą jak zwykle w podobnych przypadkach. Prokremlowska grupa wznowiła ataki DDoS w niecały tydzień po aresztowaniu dwóch jej członków i przejęciu części infrastruktury przez organy ścigania. Tymczasem Recorded Future opublikowała obszerny raport poświęcony projektowi DDoSia, który haktywiści rozwijali w ostatnich latach. Warto sięgnąć, jeśli kogoś ta tematyka interesuje. </p><p>🇬🇧 Anatomy of DDoSia: NoName057(16)'s DDoS Infrastructure and Targeting <br><a href="https://go.recordedfuture.com/hubfs/reports/cta-2025-0722.pdf" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">go.recordedfuture.com/hubfs/re</span><span class="invisible">ports/cta-2025-0722.pdf</span></a> </p><p><a href="https://infosec.exchange/tags/rosja" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>rosja</span></a> <a href="https://infosec.exchange/tags/russia" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>russia</span></a> <a href="https://infosec.exchange/tags/ddos" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>ddos</span></a> <a href="https://infosec.exchange/tags/ddosia" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>ddosia</span></a> <a href="https://infosec.exchange/tags/tymczasemwRosji" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>tymczasemwRosji</span></a></p>
John Kristoff<p>Weekend Reads</p><p>* FreeBSD Journal <a href="https://freebsdfoundation.org/our-work/journal/browser-based-edition/networking-3/" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">freebsdfoundation.org/our-work</span><span class="invisible">/journal/browser-based-edition/networking-3/</span></a><br>* Anatomy of DDoSia <a href="https://www.recordedfuture.com/research/anatomy-of-ddosia" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://www.</span><span class="ellipsis">recordedfuture.com/research/an</span><span class="invisible">atomy-of-ddosia</span></a><br>* Dataplane BGP hijack mitigation <a href="https://arxiv.org/abs/2507.14842" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="">arxiv.org/abs/2507.14842</span><span class="invisible"></span></a><br>* Formal specifications for protocols <a href="https://cacm.acm.org/research/it-takes-a-village-bridging-the-gaps-between-current-and-formal-specifications-for-protocols/" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">cacm.acm.org/research/it-takes</span><span class="invisible">-a-village-bridging-the-gaps-between-current-and-formal-specifications-for-protocols/</span></a><br>* PyPI ecosystem vulnerability analysis <a href="https://arxiv.org/abs/2507.18075" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="">arxiv.org/abs/2507.18075</span><span class="invisible"></span></a></p><p><a href="https://infosec.exchange/tags/FreeBSD" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>FreeBSD</span></a> <a href="https://infosec.exchange/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a> <a href="https://infosec.exchange/tags/BGP" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>BGP</span></a> <a href="https://infosec.exchange/tags/Protocols" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Protocols</span></a> <a href="https://infosec.exchange/tags/Python" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Python</span></a></p>
jbz<p>🕸️ How the Free Software Foundation Battles the LLM Bots • The New Stack </p><p>「 Some websites use Anubis, which sends out a JavaScript program requiring computation before allowing site access. But though it matches the FSF’s definition of free software, “we do not support this scheme because it conflicts with the principles of software freedom… a program which does calculations that a user does not want done is a form of malware,” DeVault said 」</p><p><a href="https://thenewstack.io/how-the-free-software-foundation-battles-the-llm-bots/" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">thenewstack.io/how-the-free-so</span><span class="invisible">ftware-foundation-battles-the-llm-bots/</span></a></p><p><a href="https://indieweb.social/tags/fsf" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>fsf</span></a> <a href="https://indieweb.social/tags/ddos" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>ddos</span></a> <a href="https://indieweb.social/tags/anubis" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>anubis</span></a></p>
MassivelyOP<p>Albion Online is struggling with fresh DDOS attacks – again – ostensibly from banned RMT botters<br>🔗 <a href="https://massivelyop.com/2025/07/24/albion-online-is-struggling-with-fresh-ddos-attacks-again-ostensibly-from-banned-rmt-botters" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">massivelyop.com/2025/07/24/alb</span><span class="invisible">ion-online-is-struggling-with-fresh-ddos-attacks-again-ostensibly-from-banned-rmt-botters</span></a><br><a href="https://mastodon.social/tags/AlbionOnline" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>AlbionOnline</span></a> <a href="https://mastodon.social/tags/MMORPG" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>MMORPG</span></a> <a href="https://mastodon.social/tags/DDOS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDOS</span></a></p>
Mark<p><a href="https://mastodon.scot/tags/Kyiv" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Kyiv</span></a> Independent suffers <a href="https://mastodon.scot/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a> attack after publishing criticism of anti-corruption rollback</p><p>Attack reached over 10k requests/second & targeted key parts of website</p><p>It followed publication of <a href="https://mastodon.scot/tags/critical" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>critical</span></a> <a href="https://mastodon.scot/tags/editorial" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>editorial</span></a> & in-depth coverage of the government’s push to expand the prosecutor general’s control over the National <a href="https://mastodon.scot/tags/Anti" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Anti</span></a>-Corruption Bureau (NABU) & Specialized Anti-Corruption Prosecutor’s Office (SAPO).</p><p><a href="https://kyivindependent.com/kyiv-independent-hit-by-major-ddos-attack-after-criticism-of-law-weakening-anti-graft-agencies/" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">kyivindependent.com/kyiv-indep</span><span class="invisible">endent-hit-by-major-ddos-attack-after-criticism-of-law-weakening-anti-graft-agencies/</span></a></p><p><a href="https://mastodon.scot/tags/Ukraine" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Ukraine</span></a> <a href="https://mastodon.scot/tags/NABU" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>NABU</span></a> <a href="https://mastodon.scot/tags/SAPO" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>SAPO</span></a> <a href="https://mastodon.scot/tags/justice" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>justice</span></a> <a href="https://mastodon.scot/tags/StandWithUkraine" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>StandWithUkraine</span></a> <a href="https://mastodon.scot/tags/CyberAttacks" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>CyberAttacks</span></a></p>
Kyiv Independent Daily Headlines<p><strong>Thursday, July 24, 2025</strong></p>
<p>Fire engulfs iconic Odesa market amid Russian attack — China covertly supplying drone engines to Russia despite sanctions, Reuters reports — Over half of MPs suspected by NABU backed law curbing anti-corruption agency’s independence — Ukrainian soldiers slam Zelensky’s anti-corruption crackdown … and more</p>
<p><a href="https://activitypub.writeworks.uk/2025/07/thursday-july-24-2025/" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">activitypub.writeworks.uk/2025</span><span class="invisible">/07/thursday-july-24-2025/</span></a></p>
OTX Bot<p>Threat Actors Exploit Linux SSH Servers with SVF Botnet</p><p>Cybersecurity researchers have uncovered a new attack campaign in which threat<br>actors are targeting Linux SSH servers with weak credentials to deploy the, SVF<br>botnet a Python based DDoS malware. This botnet uses Discord as its command-<br>and-control (C2) platform allowing attackers to manage infected servers in real<br>time. The SVF botnet is capable of launching Layer 7 (HTTP flood) and Layer 4<br>(UDP flood) DDoS attacks turning compromised servers into powerful tools for<br>disrupting targeted systems.</p><p>Pulse ID: 6880a810b601758421acd5a4<br>Pulse Link: <a href="https://otx.alienvault.com/pulse/6880a810b601758421acd5a4" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">otx.alienvault.com/pulse/6880a</span><span class="invisible">810b601758421acd5a4</span></a> <br>Pulse Author: cryptocti<br>Created: 2025-07-23 09:14:56</p><p>Be advised, this data is unverified and should be considered preliminary. Always do further verification.</p><p><a href="https://social.raytec.co/tags/CyberSecurity" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>CyberSecurity</span></a> <a href="https://social.raytec.co/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a> <a href="https://social.raytec.co/tags/Discord" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Discord</span></a> <a href="https://social.raytec.co/tags/DoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DoS</span></a> <a href="https://social.raytec.co/tags/HTTP" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>HTTP</span></a> <a href="https://social.raytec.co/tags/InfoSec" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>InfoSec</span></a> <a href="https://social.raytec.co/tags/Linux" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Linux</span></a> <a href="https://social.raytec.co/tags/Malware" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Malware</span></a> <a href="https://social.raytec.co/tags/OTX" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>OTX</span></a> <a href="https://social.raytec.co/tags/OpenThreatExchange" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>OpenThreatExchange</span></a> <a href="https://social.raytec.co/tags/Python" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Python</span></a> <a href="https://social.raytec.co/tags/SSH" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>SSH</span></a> <a href="https://social.raytec.co/tags/UDP" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>UDP</span></a> <a href="https://social.raytec.co/tags/bot" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>bot</span></a> <a href="https://social.raytec.co/tags/botnet" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>botnet</span></a> <a href="https://social.raytec.co/tags/cryptocti" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>cryptocti</span></a></p>
AAKL<p>Recorded Future: Anatomy of DDoSia: NoName057(16)'s DDoS Infrastructure and Targeting <a href="https://www.recordedfuture.com/research/anatomy-of-ddosia" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://www.</span><span class="ellipsis">recordedfuture.com/research/an</span><span class="invisible">atomy-of-ddosia</span></a> <a href="https://infosec.exchange/tags/cybersecurity" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>cybersecurity</span></a> <a href="https://infosec.exchange/tags/infosec" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>infosec</span></a> <a href="https://infosec.exchange/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a></p>
TugaTech 🖥️<p>Google declara guerra à Badbox 2.0: a botnet que infetou 10 milhões de Androids<br>🔗 <a href="https://tugatech.com.pt/t69614-google-declara-guerra-a-badbox-2-0-a-botnet-que-infetou-10-milhoes-de-androids" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">tugatech.com.pt/t69614-google-</span><span class="invisible">declara-guerra-a-badbox-2-0-a-botnet-que-infetou-10-milhoes-de-androids</span></a></p><p><a href="https://masto.pt/tags/android" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>android</span></a> <a href="https://masto.pt/tags/backdoor" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>backdoor</span></a> <a href="https://masto.pt/tags/ddos" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>ddos</span></a> <a href="https://masto.pt/tags/fraude" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>fraude</span></a> <a href="https://masto.pt/tags/google" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>google</span></a> <a href="https://masto.pt/tags/internet" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>internet</span></a> <a href="https://masto.pt/tags/judicial" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>judicial</span></a> <a href="https://masto.pt/tags/malware" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>malware</span></a> <a href="https://masto.pt/tags/seguran%C3%A7a" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>segurança</span></a> <a href="https://masto.pt/tags/software" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>software</span></a> <a href="https://masto.pt/tags/streaming" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>streaming</span></a> </p>
ITSEC News<p>Europol targets Kremlin-backed cybercrime gang NoName057(16) - The hacking group NoName057(16) has been operating since 2022, launching cyber attacks on... <a href="https://www.bitdefender.com/en-us/blog/hotforsecurity/europol-targets-kremlin-backed-cybercrime-gang-noname057-16" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://www.</span><span class="ellipsis">bitdefender.com/en-us/blog/hot</span><span class="invisible">forsecurity/europol-targets-kremlin-backed-cybercrime-gang-noname057-16</span></a> <a href="https://schleuss.online/tags/denialofservice" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>denialofservice</span></a> <a href="https://schleuss.online/tags/guestblog" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>guestblog</span></a> <a href="https://schleuss.online/tags/law%E2%84%B4" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>lawℴ</span></a> <a href="https://schleuss.online/tags/ukraine" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>ukraine</span></a> <a href="https://schleuss.online/tags/russia" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>russia</span></a> <a href="https://schleuss.online/tags/ddos" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>ddos</span></a></p>
অর্ঘ্য 🏏📚 💻<p>An international operation coordinated by <a href="https://mastodon.social/tags/Europol" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Europol</span></a> has disrupted the infrastructure of a pro - <a href="https://mastodon.social/tags/Russian" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Russian</span></a> <a href="https://mastodon.social/tags/hacktivist" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>hacktivist</span></a> group known as <a href="https://mastodon.social/tags/NoName057" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>NoName057</span></a>(16) that has been linked to a string of distributed denial-of-service (aka <a href="https://mastodon.social/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a>) attacks against <a href="https://mastodon.social/tags/Ukraine" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Ukraine</span></a> & its allies.</p><p>🔗 <a href="https://thehackernews.com/2025/07/europol-disrupts-noname05716-hacktivist.html" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">thehackernews.com/2025/07/euro</span><span class="invisible">pol-disrupts-noname05716-hacktivist.html</span></a></p>
Christoph Schmees<p>Russisches DDoS Botnet abgeschaltet</p><p>Das BKA meldet einen Erfolg gegen politisch motivierte Cyber-Kriminalität. Weitere Sekundär-Meldungen gibt es beispielsweise hier oder hier. Die russische Formation NoName057(16) hat ihr gleichnamiges Botnet nur für DDoS-Angriffe benutzt - soweit wir bisher wissen. Die Angriffe richteten sich gegen "unliebsame" </p><p><a href="https://www.pc-fluesterer.info/wordpress/2025/07/20/russisches-ddos-botnet-abgeschaltet/" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://www.</span><span class="ellipsis">pc-fluesterer.info/wordpress/2</span><span class="invisible">025/07/20/russisches-ddos-botnet-abgeschaltet/</span></a></p><p><a href="https://social.tchncs.de/tags/Allgemein" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Allgemein</span></a> <a href="https://social.tchncs.de/tags/Hintergrund" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Hintergrund</span></a> <a href="https://social.tchncs.de/tags/botnet" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>botnet</span></a> <a href="https://social.tchncs.de/tags/cybercrime" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>cybercrime</span></a> <a href="https://social.tchncs.de/tags/ddos" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>ddos</span></a> <a href="https://social.tchncs.de/tags/politik" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>politik</span></a></p>
Manuel 'HonkHase' Atug<p>Wer sich hinter NoName057(16) verbirgt</p><p>"Manuel Atug, <span class="h-card" translate="no"><a href="https://chaos.social/@AG_KRITIS" class="u-url mention" rel="nofollow noopener" target="_blank">@<span>AG_KRITIS</span></a></span> : Was ist ein <a href="https://chaos.social/tags/DDos" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDos</span></a>-Angriff?</p><p>DDos-Angriff funktionieren über sehr viele Serversysteme, die sehr groß ans Internet angebunden sind...</p><p>Wird das neue Sicherheitsgesetz <a href="https://chaos.social/tags/NIS2" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>NIS2</span></a> die <a href="https://chaos.social/tags/Beh%C3%B6rden" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Behörden</span></a> künftig in die <a href="https://chaos.social/tags/Absicherungspflicht" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Absicherungspflicht</span></a> nehmen?</p><p>Atug: Die meisten Behörden und öffentlichen Einrichtungen haben (DDos-Angriffe) unzureichend adressiert, weil es keine rechtlichen Vorgaben gibt..."<br><a href="https://www.mdr.de/nachrichten/deutschland/panorama/angriff-auf-die-infrastruktur-wer-sich-hinter-noname-verbirgt100.html" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://www.</span><span class="ellipsis">mdr.de/nachrichten/deutschland</span><span class="invisible">/panorama/angriff-auf-die-infrastruktur-wer-sich-hinter-noname-verbirgt100.html</span></a></p>
Hackread.com<p>In an operation called Eastwood, authorities arrested two people and shut down more than 100 servers linked to the Russian group NoName057(16).</p><p>Read: <a href="https://hackread.com/police-shut-down-100-servers-russian-noname05716/" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">hackread.com/police-shut-down-</span><span class="invisible">100-servers-russian-noname05716/</span></a></p><p><a href="https://mstdn.social/tags/CyberSecurity" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>CyberSecurity</span></a> <a href="https://mstdn.social/tags/CyberCrime" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>CyberCrime</span></a> <a href="https://mstdn.social/tags/Russia" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Russia</span></a> <a href="https://mstdn.social/tags/NoName057" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>NoName057</span></a>(16) <a href="https://mstdn.social/tags/Europe" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Europe</span></a> <a href="https://mstdn.social/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a></p>
Max Resing<p>Sehr cool. Heute gab es auch schon wieder ein Sign-of-Life von <a href="https://infosec.exchange/tags/NoName05716" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>NoName05716</span></a> auf X:</p><p><a href="https://x.com/noname05716/status/1945785985595474348" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://</span><span class="ellipsis">x.com/noname05716/status/19457</span><span class="invisible">85985595474348</span></a></p><p>Angeblich wieder aktiv, mit neuen <a href="https://infosec.exchange/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a> zielen auf deutsche Infrastruktur.</p>
Manuel 'HonkHase' Atug<p>Heute Abend ab 19:30 Uhr bin ich für die <span class="h-card" translate="no"><a href="https://chaos.social/@AG_KRITIS" class="u-url mention" rel="nofollow noopener" target="_blank">@<span>AG_KRITIS</span></a></span> bei MDR Aktuell in den Nachrichten mit dabei zur <a href="https://chaos.social/tags/BKA" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>BKA</span></a> Meldung gegen die <a href="https://chaos.social/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a>-Bande NoName057(16) und wie schlecht der <a href="https://chaos.social/tags/KRITIS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>KRITIS</span></a> Sektor <a href="https://chaos.social/tags/Staat" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Staat</span></a> und <a href="https://chaos.social/tags/Verwaltung" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Verwaltung</span></a> dazu aufgestellt ist.</p><p><a href="https://www.mdr.de/mdr-aktuell-nachrichtenradio/index.html" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://www.</span><span class="ellipsis">mdr.de/mdr-aktuell-nachrichten</span><span class="invisible">radio/index.html</span></a></p>
Prof. Dr. Dennis-Kenji Kipker<p><a href="https://chaos.social/tags/DDoS" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>DDoS</span></a> als gezielter Eingriff in die staatliche <a href="https://chaos.social/tags/Souver%C3%A4nit%C3%A4t" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Souveränität</span></a>: Massenhafte Überlastungsattacken sind nicht nur eine ernsthafte Gefahr für die <a href="https://chaos.social/tags/Cybersecurity" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Cybersecurity</span></a>, sondern ebenso für das staatliche Gemeinwesen, indem auch öffentliche Infrastrukturen für Bürger:innen blockiert werden.</p><p>Nachdem es in den letzten Wochen verstärkt DDoS-Angriffe gab, wurden nun die hinter der prorussischen <a href="https://chaos.social/tags/Hackergruppe" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>Hackergruppe</span></a> <a href="https://chaos.social/tags/NoName057" class="mention hashtag" rel="nofollow noopener" target="_blank">#<span>NoName057</span></a>(16) stehenden Personen ermittelt und das Servernetz abgeschaltet:</p><p><a href="https://www.tagesschau.de/inland/servernetz-hacker-100.html" rel="nofollow noopener" translate="no" target="_blank"><span class="invisible">https://www.</span><span class="ellipsis">tagesschau.de/inland/servernet</span><span class="invisible">z-hacker-100.html</span></a></p>
Importante operazione internazionale coordinata da @Europol espone infrastruttura e avvia arresti, denunce e mandati di sequestro ai danni del gruppo criminale #NoName05716 .
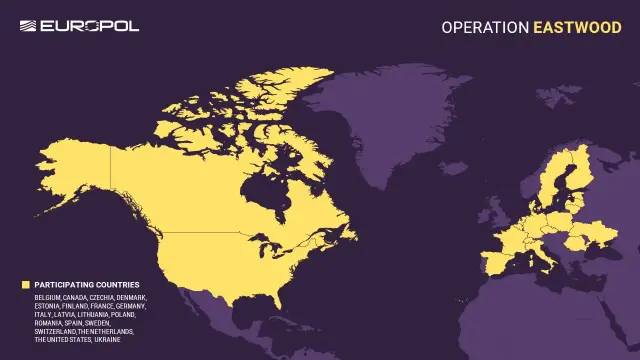
Cyber Security 360 · Operazione Eastwood contro NoName057(16): così l'Europa ha fermato gli attacchi DDoS pro-russi - Cyber Security 360Coordinato da Europol ed Eurojust, il blitz internazionale ribattezzato "Operazione Eastwood" ha consentito di smantellare l’infrastruttura dietro una delle più attive campagne DDoS filo-Cremlino. Ecco tutti i dettagli di una importante vittoria in una guerra ancora lunga contro la minaccia ibrida
TrendingLive feeds
Mastodon is the best way to keep up with what's happening.
Follow anyone across the fediverse and see it all in chronological order. No algorithms, ads, or clickbait in sight.
Create accountLoginDrag & drop to upload